Log Users Out of Auth0 with OIDC Endpoint
Auth0 implements OpenID Connect’s RP-Initiated Logout 1.0 for end-user logout. This standard is part of the OpenID Connect collection of final specifications.
How it works
RP-Initiated Logout is a scenario in which a relying party (user) requests the OpenID provider (Auth0) to log them out.
The user initiates a logout request in your application.
Your application directs the user to the Auth0 Authentication API OIDC Logout endpoint.
Auth0 redirects the user to the appropriate destination based on the provided OIDC Logout endpoint parameters.
Configure RP-Initiated Logout
To configure RP-Initiated Logout, you must ensure that your application can find the end_session_endpoint parameter in your Auth0 tenant’s discovery metadata document, and that it calls the OIDC Logout endpoint with the necessary parameters.
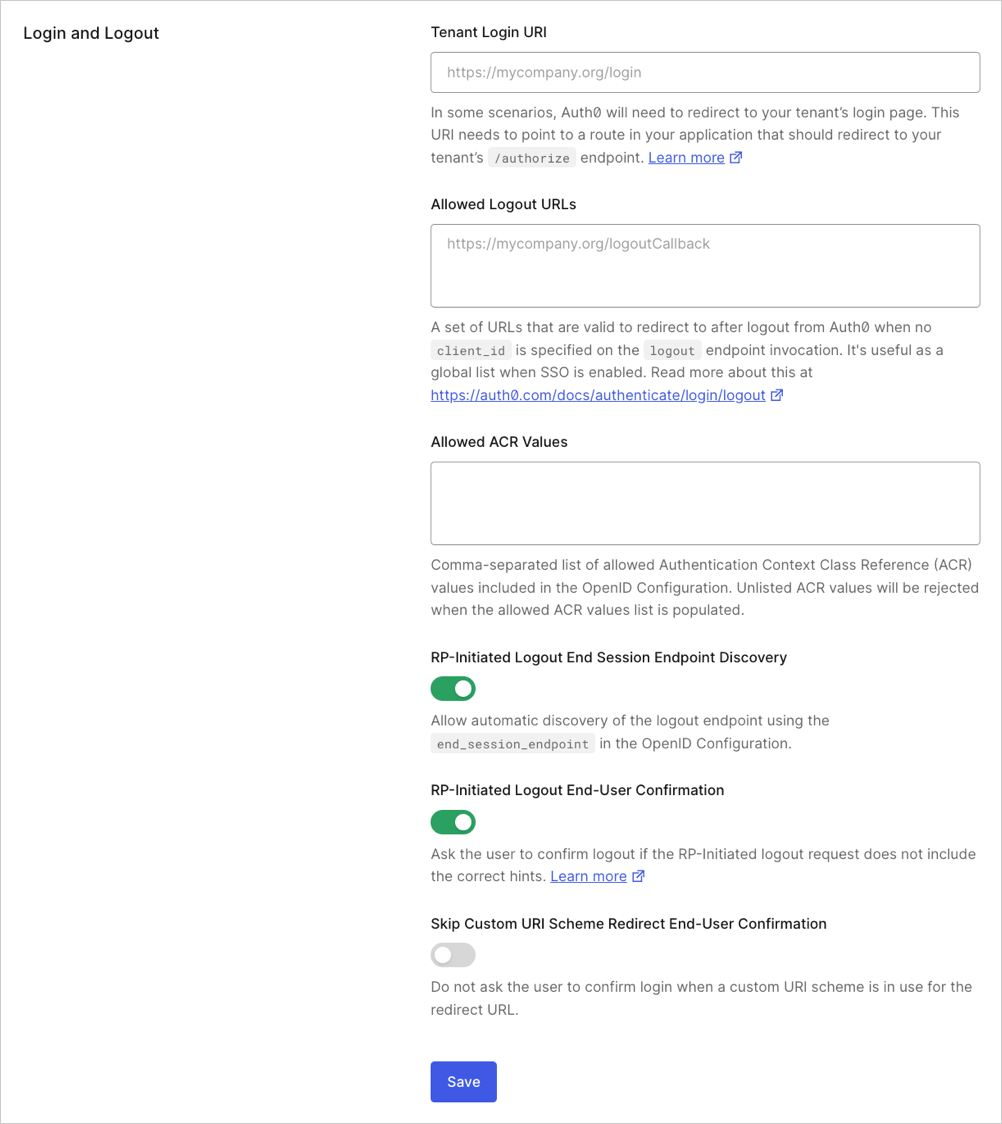
Enable endpoint discovery
You can enable RP-Initiated Logout End Session Endpoint Discovery in the Auth0 Dashboard or with the Auth0 Management API.
To enable RP-Initiated Logout End Session Endpoint Discovery in the Dashboard:
Locate the Login and Logout section.
Enable the RP-Initiated Logout End Session Endpoint Discovery toggle.
To enable RP-Initiated Logout End Session Endpoint Discovery with the Management API:
Get a Management API access token that includes the
update:tenant_settingsscope.Call the Management API Update tenant settings endpoint with the following payload:
{ "oidc_logout": { "rp_logout_end_session_endpoint_discovery": true } }Was this helpful?
/
Call the OIDC Logout endpoint
When you call the OIDC Logout endpoint, Auth0 recommends that you provide the id_token_hint parameter.
If your application cannot securely store ID tokens, you may provide the logout_hint and client_id parameters instead.
OIDC Logout endpoint parameters
The Authentication API OIDC Logout endpoint supports the following parameters:
| Parameter | Required? | Description |
|---|---|---|
id_token_hint |
Recommended | ID token previously issued for the user. That indicates which user to log out. |
logout_hint |
Optional | Session ID (sid) value that indicates which user to log out. |
post_logout_redirect_uri |
Optional | Redirect URL value that indicates where to redirect the user after logout. |
client_id |
Optional | Client ID of your application. |
federated |
Optional | Directs Auth0 to log the user out of their identity provider. |
state |
Optional | Opaque value that the application adds to the initial logout request, and that Auth0 includes when redirecting the back to the post_logout_redirect_uri. |
ui_locales |
Optional | Space-delimited list of locales used to constrain the language list for the request. The first locale on the list must match the enabled locale in your tenant. |
id_token_hint parameter
The value of the id_token_hint parameter must be the ID token that Auth0 issued to the user after they authenticated.
The ID token contains the registered claims issuer (iss), audience (aud), and the Auth0 session ID (sid) for verification. To learn more about ID token claims, read ID Token Structure.
Examples
https://{yourDomain}/oidc/logout?id_token_hint={yourIdToken}&post_logout_redirect_uri={yourCallbackUrl}Was this helpful?
curl --request GET \
--url 'https://{yourDomain}/oidc/logout' \
--header 'content-type: application/x-www-form-urlencoded' \
--data 'id_token_hint={yourIdToken}' \
--data 'post_logout_redirect_uri={yourCallbackUrl}'Was this helpful?
logout_hint parameter
The value of the logout_hint parameter must be the session ID (sid) of the user’s current Auth0 session.
The session ID (sid) is provided as a registered claim within the ID token that Auth0 issued to the user after they authenticated.
Example
https://{yourDomain}/oidc/logout?{clientId}={yourClientId}&logout_hint={sessionId}Was this helpful?
post_logout_redirect_uri parameter
The value of the post_logout_redirect_uri parameter must be a valid, encoded URL that has been registered in the list of Allowed Logout URLs in your:
Application settings: If you provide the
id_token_hintparameter, or thelogout_hintandclient_idparameters.Tenant settings: If you provide only the
logout_hintparameter.
Example
https://{yourDomain}/oidc/logout?post_logout_redirect_uri=http%3A%2F%2Fwww.example.comWas this helpful?
Update application Allowed Logout URLs
You can register a URL with your application’s list of Allowed Logout URLs in the Auth0 Dashboard or with the Auth0 Management API.
To register a URL with your application’s list of Allowed Logout URLs in the Dashboard:
Select your application.
Locate the Application URIs section.
Update Allowed Logout URLs following the provided guidelines.
To register a URL with your application’s list of Allowed Logout URLs with the Management API:
Get a Management API access token that includes the
update:clientsscopes.Call the Management API Update a client endpoint, and ensure that you include the URL in the value of the
allowed_logout_urlsfield within the request body.PATCH https://{yourDomain}/api/v2/clients/{clientId} Authorization: Bearer {yourMgmtApiAccessToken} Content-Type: application/json { "allowed_logout_urls": [ "https://www.example.com", "https://www.example.com/logout" ] }Was this helpful?
/
Update tenant Allowed Logout URLs
You can register a URL with your tenant’s list of Allowed Logout URLs in the Auth0 Dashboard or with the Auth0 Management API.
To register a URL with your tenant’s list of Allowed Logout URLs in the Dashboard:
Locate the Login and Logout section.
Update Allowed Logout URLs following the provided guidelines.
To register a URL with your tenant’s list of Allowed Logout URLs with the Management API:
Get a Management API access token that includes the
update:tenant_settingsscopes.Call the Management API Update tenant settings endpoint, and ensure that you include the URL in the value of the
allowed_logout_urlsfield within the request body.PATCH https://{yourDomain}/api/v2/tenants/settings Authorization: Bearer {yourMgmtApiAccessToken} Content-Type: application/json { "allowed_logout_urls": [ "https://www.example.com", "https://www.example.com/logout" ] }Was this helpful?
/
Allowed Logout URLs guidelines
When you update Allowed Logout URLs, follow the guidelines below to avoid validation errors:
Separate multiple URL values with a comma (
,).Include the URL scheme part (for example,
https://).
You may use an asterisk (*) as a wildcard for subdomains (such as https://*.example.com), but we recommend that you do not use wildcards in production environments. For more information, read Subdomain URL Placeholders.
Add query string parameters to post_logout_redirect_uri
The OIDC Logout endpoint parses query string parameters in the URL provided to the post_logout_redirect_uri parameter.
You must include these query string parameters in your Allowed Logout URLs, or the logout request may be denied.
For example, if you pass https://example.com/logout?myParam=1234 to the post_logout_redirect_uri parameter (encoded as https%3A%2F%2Fexample.com%2Flogout%3FmyParam%3D1234), you must include https://example.com/logout?myParam in your Allowed Logout URLs.
ui_locales parameter
The value of the ui_locales parameter must be a space-delimited list of supported locales.
The first value provided in the list must match your tenant’s Default Language setting.
federated parameter
The federated parameter does not require a value.
If you include the federated parameter when you call the OIDC Logout endpoint, Auth0 attempts to log the user out of their identity provider.
Logout consent prompt
The OIDC standard defines that the logout flow should be interrupted to prompt the user for consent if the OpenID provider cannot verify that the request was made by the user.
Auth0 enforces this behavior by displaying a logout consent prompt if it detects any of the following conditions:
Neither the
id_token_hintnorlogout_hintparameters are provided.The ID token's
sidclaim does not correspond to the browser session in the request.The value of the
logout_hintparameter does not match current session data.

If the user confirms the logout request, Auth0 continues the logout flow.
Disable the logout consent prompt
You may disable the logout consent prompt. If you do, Auth0 does not attempt to detect anomalous behavior and accepts logout requests automatically.
To disable the logout consent prompt in the Dashboard:
Disable the Show RP-Initiated Logout End-User Confirmation toggle.